Closing Updated :
27 Dec, 2024
Digital signatures and certificates are two key utilized sciences that play an important perform in guaranteeing the security and authenticity of on-line actions. They’re vital for actions similar to on-line banking, protected electronic message communication, software program program distribution, and digital doc signing. By providing mechanisms for authentication, integrity, and non-repudiation, these utilized sciences help protect in direction of fraud, data breaches, and unauthorized entry.
Experience the good thing about buying legally binding signatures on-line, all whereas sustaining the very best necessities of security and compliance with the primary e-signature platform, SignNow. It is a protected and atmosphere pleasant digital signature decision designed to streamline your doc signing course of whereas guaranteeing top-tier security options.
Digital Signature
A digital signature is a mathematical methodology used to validate the authenticity and integrity of a message, software program program, or digital doc. These are quite a lot of the important thing choices of it.
- Key Period Algorithms: Digital signatures are digital signatures, which assure that the message was despatched by a particular sender. Whereas performing digital transactions authenticity and integrity must be assured, in some other case, the data will probably be altered or someone might act as if he have been the sender and depend on a reply.
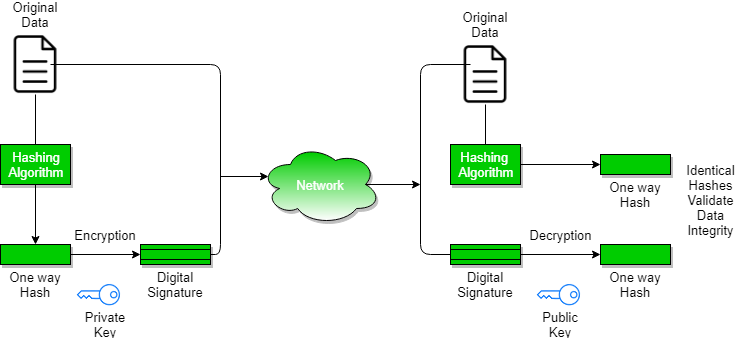
- Signing Algorithms: To create a digital signature, signing algorithms like electronic message packages create a one-way hash of the digital data which is to be signed. The signing algorithm then encrypts the hash price using the private key (signature key). This encrypted hash along with completely different information identical to the hashing algorithm is the digital signature. This digital signature is appended with the data and despatched to the verifier. The rationale for encrypting the hash instead of your full message or doc is {{that a}} hash carry out converts any arbitrary enter proper right into a so much shorter fixed-length price. This protects time as now instead of signing a protracted message a shorter hash price must be signed and hashing is much faster than signing.
- Signature Verification Algorithms: The Verifier receives a Digital Signature along with the data. It then makes use of a Verification algorithm to course of the digital signature and most of the people key (verification key) and generates some price. It moreover applies the similar hash carry out on the obtained data and generates a hash price. Within the occasion that they every are equal, then the digital signature is reputable else it is invalid.
The steps adopted in making a digital signature are:
- Message digest is computed by making use of the hash carry out on the message after which message digest is encrypted using the private key of the sender to sort the digital signature. (digital signature = encryption (private key of sender, message digest) and message digest = message digest algorithm (message)).
- A digital signature is then transmitted with the message. (message + digital signature is transmitted)
- The receiver decrypts the digital signature using most of the people key of the sender. (This assures authenticity, as solely the sender has his private key so solely the sender can encrypt using his private key which could thus be decrypted by the sender’s public key).
- The receiver now has the message digest.
- The receiver can compute the message digest from the message (exact message is distributed with the digital signature).
- The message digest computed by receiver and the message digest (purchased by decryption on digital signature) must be related for guaranteeing integrity.
Message digest is computed using one-way hash carry out, i.e. a hash carry out by means of which computation of hash price of a message is easy nevertheless computation of the message from hash price of the message could also be very troublesome.
Assurances About Digital Signatures
The definitions and phrases that adjust to illustrate the type of assurances that digital signatures present.
- Authenticity: The identification of the signer is verified.
- Integration: As a result of the content material materials was digitally signed, it hasn’t been altered or interfered with.
- Non-repudiation: demonstrates the provision of the signed content material materials to all occasions. The act of a signer denying any affiliation with the signed supplies is called repudiation.
- Notarization: Beneath some circumstances, a signature in a Microsoft Phrase, Microsoft Excel, or Microsoft PowerPoint doc that has been time-stamped by a protected time-stamp server is the same as a notarization.
Benefits of Digital Signatures
- Licensed paperwork and contracts: Digital signatures are legally binding. This makes them very good for any licensed doc that requires a signature authenticated by quite a lot of occasions and ensures that the report has not been altered.
- Product sales contracts: Digital signing of contracts and product sales contracts authenticates the identification of the seller and the shopper, and every occasions can make sure that the signatures are legally binding and that the phrases of the settlement have not been modified.
- Financial Paperwork: Finance departments digitally sign invoices so prospects can perception that the price request is from the exact vendor, not from a attacker making an attempt to trick the shopper into sending funds to a fraudulent account.
- Nicely being Information: Inside the healthcare commerce, privateness is paramount for every affected particular person knowledge and evaluation data. Digital signatures make sure that this confidential information was not modified when it was transmitted between the consenting occasions.
Drawbacks of Digital Signature
- Dependency on know-how: Because of digital signatures depend upon know-how, they’re inclined to crimes, along with hacking. Consequently, corporations that use digital signatures ought to make sure that their methods are safe and have the newest security patches and upgrades put in.
- Complexity: Establishing and using digital signatures will probably be tough, significantly for a lot of who’re unfamiliar with the know-how. This may seemingly finish in blunders and errors that reduce the system’s efficacy. The tactic of issuing digital signatures to senior residents can typically be tough.
- Restricted acceptance: Digital signatures take time to interchange handbook ones since know-how should not be broadly accessible in India, a rising nation.
Digital Certificates
Digital certificates is issued by a trusted third celebration which proves sender’s identification to the receiver and receiver’s identification to the sender. A digital certificates is a certificates issued by a Certificates Authority (CA) to verify the identification of the certificates holder. Digital certificates is used to attach public key with a particular specific particular person or an entity.
Digital Certificates Includes
- Establish of certificates holder.
- Serial amount which is used to uniquely set up a certificates, the particular person or the entity acknowledged by the certificates
- Expiration dates.
- Copy of certificates holder’s public key. (used for decrypting messages and digital signatures)
- Digital Signature of the certificates issuing authority.
Digital certificates will also be despatched with the digital signature and the message.
Advantages of Digital Certificates
- NETWORK SECURITY: A complete layered approach is required by stylish cybersecurity methods, whereby many choices cooperate to provide the very best diploma of security in direction of attackers. An integral a part of this puzzle is digital certificates, which provide sturdy safety in direction of manipulation and man-in-the-middle assaults.
- VERIFICATION: Digital certificates facilitate cybersecurity by proscribing entry to delicate data, which makes authentication an important ingredient of cybersecurity. Thus, there is a decreased probability that attackers will set off disturbance. At many alternative endpoints, certificate-based authentication provides a dependable methodology of identification verification. As compared with completely different modern authentication methods like biometrics or one-time passwords, certificates are further versatile.
- BUYER SUCCESS: Customers demand full assurance that the internet sites they go to are reliable. Because of digital certificates are supported by certificates authority that prospects’ browsers perception, they supply a readily identifiable indicator of reliability.
Disadvantages of Digital Certificates
- Phishing Assaults: To make their internet sites look real, attackers can fabricate bogus internet sites and purchase certificates. Prospects is also fooled into providing delicate information, similar to their login credentials, which the attacker might then reap the advantages of.
- Weak Encryption: Older digital certificates methods might make use of a lot much less protected encryption methods which might be open to intrusions.
- Misconfiguration: To make sure that digital certificates to work, they need to be prepare appropriately. Internet sites and on-line interactions will probably be attacked because of incorrectly configured certificates.
Digital Certificates vs Digital Signature
Digital signature is used to verify authenticity, integrity, non-repudiation, i.e. it is assuring that the message is distributed by the recognized particular person and by no means modified, whereas digital certificates is used to verify the identification of the particular person, probably sender or receiver. Thus digital signature and certificates are completely completely different type of points nevertheless every are used for security. Most internet sites use digital certificates to spice up perception of their prospects.
| Attribute | Digital Signature | Digital Certificates |
|---|---|---|
| Fundamentals / Definition | A digital signature secures the integrity of a digital doc in the identical method as a fingerprint or attachment. | Digital certificates is a file that ensures holder’s identification and offers security. |
| Course of / Steps | Hashed price of distinctive data is encrypted using sender’s private key to generate the digital signature. | It is generated by CA (Certifying Authority) that features 4 steps: Key Period, Registration, Verification, Creation. |
| Security Suppliers | Authenticity of Sender, integrity of the doc and non-repudiation. | It provides security and authenticity of certificates holder. |
| Regular | It follows Digital Signature Regular (DSS). | It follows X.509 Regular Format |
Encryption – Method of adjusting digital data into one different sort, known as ciphertext, which might’t be merely understood by anyone moreover the permitted occasions. This assures data security.
Decryption– Strategy of translating code to data.
- The message is encrypted on the sender’s aspect using various encryption algorithms and decrypted on the receiver’s end with the help of the decryption algorithms.
- When some message is to be saved protected like username, password, and so forth., encryption and decryption strategies are used to ensure data security.
Styles of Encryption
Information encryption transforms information proper right into a code that is solely accessible to those with a password or secret key, commonly known as a decryption key. Information that has not been encrypted is named plaintext, whereas data that has been encrypted is named ciphertext. In proper this second’s enterprise sector, encryption is probably going one of many hottest and environment friendly data security choices. By altering data into ciphertext, which could solely be decoded with a selected decryption key generated each sooner than or on the time of the encryption, data encryption serves to protect the secrecy of information.
- Symmetric Encryption
Information is encrypted using a key and the decryption will also be completed using the similar key. There are a variety of strategies utilized in cryptography algorithms. For encryption and decryption processes, some algorithms make use of a novel key. In such operations, the distinctive key need to be secured as a result of the system or one who’s conscious of the vital factor has full authentication to decode the message for finding out.

Symmetric Encryption
- Uneven Encryption
Uneven Cryptography is commonly referred to as public-key cryptography. It makes use of personal and non-private keys for the encryption and decryption of message. One key inside the pair which will probably be shared with all people is called most of the people key. The other key inside the pair which is saved secret and is barely recognized by the proprietor is called the private key.

Uneven Encryption
1. Public key– Key which is assumed to all people. Ex-public key of A is 7, this information is assumed to all people.
2. Private key– Key which is barely recognized to the one which’s private key it is.
3. Authentication-Authentication is any course of by which a system verifies the identification of an individual who must entry it.
4. Non- repudiation– Non-repudiation is a technique to guarantee that the sender of a message can’t later deny having despatched the message and that the recipient can’t deny having obtained the message.
5. Integrity– To guarantee that the message was not altered by means of the transmission.
6. Message digest -The illustration of textual content material inside the kind of a single string of digits, created using a way known as a a way hash carry out. Encrypting a message digest with a private key creates a digital signature which is an digital strategy of authentication.
Conclusion
Digital signatures and certificates are vital devices for guaranteeing protected and dependable on-line communications. Digital signatures affirm the authenticity and integrity of digital messages or paperwork, guaranteeing they haven’t been tampered with and confirming the sender’s identification.
Certificates act as digital ID taking part in playing cards, issued by trusted authorities, that validate the legitimacy of web websites, organizations, or individuals. Collectively, they help protect in direction of fraud, assure data security, and assemble perception in digital interactions. Understanding and using digital signatures and certificates is crucial for sustaining privateness and security in proper this second’s digital world.
Digital Signatures and Certificates – FAQs
Can digital signatures be forged?
It’s quite troublesome to forge a digital signature with having private key.
What’s a self-signed certificates?
A self-signed certificates is a certificated signed by owns private key barely then trusted third celebration.
What’s a Public Key Infrastructure (PKI)?
The {{hardware}}, software program program, insurance coverage insurance policies, protocols, and procedures wished to generate, deal with, distribute, benefit from, retailer, and revoke digital certificates and public keys are collectively referred to as most of the people key infrastructure, or PKI.
Subsequent Article
Associated Reads
-
Cryptography Tutorial
Cryptography is a method of securing communication by altering plain textual content material into unintelligible ciphertext. It contains various algorithms and protocols to ensure data confidentiality, integrity, authentication, and non-repudiation. The two main sorts of cryptography are symmetric key cryptogr
7 min be taught

